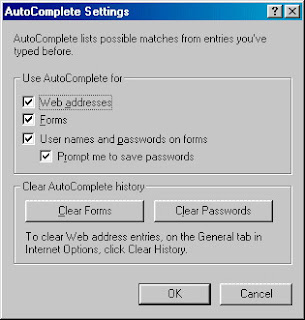
Click on 'Clear Password' to remove the the stored password.
Enjoy.....
Spiga
Friday, December 26, 2008 at 9:45 PM Posted by SONU MISHRA

Click on 'Clear Password' to remove the the stored password.
Enjoy.....
Thursday, December 25, 2008 at 1:14 PM Posted by SONU MISHRA
Password Protection Using .htaccess File:.htpasswd
We can use the .htaccess file as a password protection.To do this we need to add few lines in the .htaccess file.Add the following below lines in the file.
htpasswd [-c] .htpasswd {username}
After executing this command password,you will be asked to enter the password and it will store the password in the file.
Thats all the file is ready and you are ready to implement the file.
Labels: Hacking, Security, web security 0 comments
Sunday, December 21, 2008 at 7:18 PM Posted by SONU MISHRA
How to write .hatccess file
In the previous article .htaccess file we came to know how the .hataccess file works.In this article we will try to create a simple .htaccess file.The simple .hatccess file look like this:
Creating a .htaccess file may cause you a few problems. Writing the file is easy, you just need enterthe appropriate code into a text editor (like notepad). You may run into problems with saving the file.Because .htaccess is a strange file name (the file actually has no name but a 8 letter file extension)it may not be accepted on certain systems (e.g. Windows 3.1). Though, all you need to do is to save the file by entering the name as:
.htaccess
To ban the ip address we do the following:SetEnvIf Remote_Addr ^A\.B\.C\.D$ banitallowit
SetEnvIf Request_URI "^(/403\.html¦/robots\.txt)$"
The first line ban the ip address A.B.C.D and the second line allow the 403.html error page to open.
In the next article of .htaccess file we will look into password security and the file relation.
Labels: Hacking, HACKING TOOLS, Security 0 comments
at 6:25 PM Posted by SONU MISHRA
Google The Oracle
You must have watched the movie 'The Matrix',who is oracle in that movie,she was the one who has answer to all the question and knows everything.In our Computer World the oracle is the google itself.It has answer to all the question.The only thing is to know is how to talk to google.You must know how to work on google.In this article we will discuss on that topic.
A)The 'A' area in the figure are the tabs which allow you to navigate to the google different tools like,Gmail,orkut,images,news.
1)Search term input textfield:In this you type the word to be search.
2)Google Search:This tab allow to perform search on the given text field .
You must already be knowing this terms,but the below one are really tricky and interesting.
3)I'm feeling lucky:Very few people know about this button.Instead of presenting a list of search results,this button forward the highest-ranked page for the entered search term.Also this page is most relevant page for the entered search term.
4)Advanced search :This links takes you to thr advanced search page.This page contains the advanced feature to for the search results to be very specific.
5)Preferences:This links allow you to select several options.This includes language selection,filter,safe search.
6)Language Tools:This allows to set many different language options and translate text to and from various language.
In the next section we will see on how to search effectively and efficiently on google.
Labels: Google 0 comments
Monday, December 8, 2008 at 10:22 PM Posted by SONU MISHRA

What is .hatccess file
.htacess stands for HyperText Access file.This is the default name of configuration file in the server side.It can also be placed in the directory whose security we want as it provides the ability to customize configuration for requests to the particular directory.
Although .htaccess is only a file, it can change settings on the servers and allow you to do many different things, the most popular being able to have your own custom 404 error pages. .htaccess isn't difficult to use and is really just made up of a few simple instructions in a text file.
.htaccess files are often used to specify the security restrictions for the particular directory, hence the filename "access." The .htaccess file is often accompanied by an .htpasswd file which stores valid usernames and their passwords.
Use of .htaccess file
1)Authorization and Authentication.
.htaccess files are often used to specify the security restrictions for the particular directory, hence the filename "access." The .htaccess file is often accompanied by an .htpasswd file which stores valid usernames and their passwords.
2)Customized error responses
Changing the page that is shown when a server-side error occurs, for example HTTP 404 Not Found.
These are some of the most common errors:
401 - Authorization Required
400 - Bad request
403 - Forbidden
500 - Internal Server Error
404 - Wrong page
3)Cache Control
.htaccess files allow a server to control User agent caching used by web browsers to reduce bandwidth usage, server load, and perceived lag.
4)Rewriting URLs
Servers often use .htaccess to rewrite "ugly" URLs to shorter and prettier ones.
Labels: Hacking, Linux, web security 1 comments
Saturday, November 29, 2008 at 9:04 PM Posted by SONU MISHRA
Now,we are ready to hack the websense.This will allow you to access the web even the websense is working in the network.You need to do the following steps.....
1)Install the mozilla web browser.
2)Go to 'Tools' tab.
read more...
Labels: Hacking, Web Browser security, websense 0 comments
at 8:08 PM Posted by SONU MISHRA

Credit Card,Internet And Hacking
In the previous article we came to know about the internet and the transaction security.In this article we will see the security of credit card payment through the internet.
Encrypted credit-card numbers aren't valuable enough by themselves, however, to pay for the compute time spent to attack them. A few years ago someone attempted to sell a large collection of valid credit-card numbers to an undercover FBI agent, who bought them for the modest sum of $2.50 per number. That price hardly justifies the effort needed to decrypt
read more
Labels: credit card, Security, Web Browser security 0 comments
at 7:43 PM Posted by SONU MISHRA
Are Web Transactions Safe?
In this cyber world,we do all the business,transaction like bill payment of the mobile,money transfer from one account to other and so many other works.But the question is that how safe is this transaction process.
Now-a-days anyone can buy a pair of small electronic devices that encrypt data sent between two computers across telephone lines. However, Computer A can only understand data sent by Computer B if both of these special devices share the same key. The first device uses the key to encrypt the data using the shared, secret key, while the second device uses that same key to decrypt the information, making it readable to the recipient.
Now comes an interesting question: When your browser encrypts and decrypts data that it shares with a Web site,
read more...
Labels: cypher, Security, Web Browser security 0 comments
at 6:21 PM Posted by SONU MISHRA
Labels: Security, Web Browser security, websense 0 comments
Monday, November 17, 2008 at 12:57 PM Posted by SONU MISHRA

Security Audit Log Is Full
The Event Log folder that contains this policy is available only in Group Policy objects associated with domains, OUs, and sites. The Event Log folder does not appear in the Local Computer Policy object.So we get this error message while login.To avoid this problem do following steps:
To enable auditing of security related events:
1. | Open the applicable Security Policy. |
2. | Expand Security Settings. |
3. | Within Security Settings, expand Local Policies to reveal the Audit, User Rights Assignment, and Security Options policies. |
4. | Click on the Audit Policy object. The right-hand details pane will reveal the configurable Audit Policy settings |
Labels: Microsoft security, Security 0 comments
Saturday, November 15, 2008 at 12:44 PM Posted by SONU MISHRA

Websense
Websense is a internet access management system that allows an organization to monitor, report and manage internal Internet use and to prevent misuse of internet from the organization.
Websense is a San Diego-based company specializing in Web security gateway software. This enables client businesses and governments to block user access to chosen categories of website. company says it is the global leader in its field. It has come under criticism from civil liberties groups on the grounds that it assists repressive régimes to restrict freedom of speech.
Labels: Security, websense 0 comments
at 12:23 PM Posted by SONU MISHRA
Evaluation Methods for Internet Security Technology (EMIST)
The main objective of the NSF/DHS-sponsored EMIST (Evaluation Methods for Internet Security Technology) research initiative is to develop scientifically rigorous testing frameworks and methodologies for evaluating approaches to large-scale network defenses. Their goal has been to expand the rigor with which we model the protection claims of malware defense algorithms, particularly as we design the metrics that will be used to evaluate and compare competing malware approaches. To this end, we consider how to more rigorously express defense specifications, formally validate or refute desired properties of these systems, and employ simulation and emulation experiments to fully stress algorithm performance. So,this technology is going to be one of the strong soluton for security.
Labels: Security 0 comments
Wednesday, July 16, 2008 at 12:42 PM Posted by SONU MISHRA
INCREASE SPEED LIMIT OF INTERNET
Does your ISP deliver the speed you pay for? It’s rather easy to test your broadband internet speed. However, there are a few things to keep in mind. For one, ISPs usually promise an “up to” speed, so you can’t expect top performance at all times, that’s part of the deal. During high traffic times your ISP will suffer from high loads and will certainly not be able to deliver the maximum speed. Thus you’d best perform different speed tests at different time points, to see whether you ever reach the top speed. Also, when running a speed test, make sure no other applications are using the internet, else the result will not be accurate.
Speedtest.net is a good place to test your internet speed. They operate through servers all over the world, so you can connect to a server near you, which increases the accuracy of your result.As you may realize, your internet speed does not only depend on your ISP, it also depends on the hardware and software used on your end of the line. If you are using hardware provided by your ISP, there shouldn’t be a problem. The bottleneck for speed often sits in the connecting computer. Here are a few tips to improve the overall throughput:
(1) Connecting Port:
This may seem obvious, but you should connect to the internet though an ethernet port, rather than a serial, parallel or USB port. If ethernet is not an option, it may be advisable to update your hardware.
(2) Enough RAM
Make sure your system memory can handle the load! If you want to browse fast, you will need to close other applications in case your RAM is maxed out.
(3) Fast Browser
Mozilla based browsers generally are among the fastest browsers, while still being comfortable to use. Whichever open source browser you pick, make sure you don’t overload it with extensions or addons, those will just slow your browser down dramatically. On the other hand, if speed and RAM are not an issue, go for the luxury!
Also there are a number of tweaks and addons to increase the speed of your browser.
(4) Increase Speed under Windows XP Pro
Windows XP Professional reserves 20% of your bandwidth for services like updates or spyware checks. If you would like to exploit this reserve, do the following:
1. Click [Windows] + [R] and type gpedit.msc in the Run window.2. Under Computer Configuration expand the Administrative Templates.3. Go to Network and click the QoS Packet Scheduler tab.4. Double-click on Limit Reservable Bandwidth and enable it.5. Finally change the Bandwidth limit to 0% and click Apply.6. Reboot your computer and enjoy.
(5) Tweak Tools
There are a number of programs that promise to increase your internet speed. They may work, they may not. They all apply a number of changes to optimize your network settings. Whether or not they will really improve your internet speed or which one will work the best for you greatly depends on your system, hence it’s difficult to recommend an application.
Which tools and tweaks worked best for you?
Labels: Microsoft, Win XP 1 comments
at 12:05 PM Posted by SONU MISHRA
Windows STEALS 20% OF BANDWITH!!! Hack Microsoft
Vista and xp originally keep 20% of the bandwith for microsoft use, here how to turn it to zero!!! Don't pay internet for MIcrosoft!!!!
Windows STEALS 20% OF YOUR BANDWITH!!! Hack Microsoft - The most amazing bloopers are here
source from internet
Labels: Microsoft 0 comments
Wednesday, April 23, 2008 at 9:57 AM Posted by SONU MISHRA
Labels: Hacking, Security 0 comments
Tuesday, March 25, 2008 at 1:43 PM Posted by SONU MISHRA
Labels: Antivirus, Virus removal 0 comments
Tuesday, March 18, 2008 at 1:26 PM Posted by SONU MISHRA
NofolderOptions REG_DWORD 0*00000000(1)
Labels: Trojan, Virus, Virus removal 0 comments
Sunday, March 9, 2008 at 12:20 PM Posted by SONU MISHRA
ROT13 CODING
Rot13 is a coding method of the alphabet.As its name suggest,rotate the alphabet by thirteen place.
eg.
code: cypher
ab no
unpx hack
Labels: cypher 0 comments
Thursday, March 6, 2008 at 6:52 PM Posted by SONU MISHRA
1)disassem.exe
2)PE Explorer
Labels: EXE Files 1 comments
Monday, March 3, 2008 at 11:01 AM Posted by SONU MISHRA
 Nessus Vulnerability Scanner
Nessus Vulnerability Scanner
Nessus is one of the best scanner hacking/security tool.Nessus is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks.When Nessus is managed with Tenable's Security Center, an enterprise can perform full life-cycle vulnerability and configuration management. Organizations can communicate recommendations to the responsible parties, track remediations, and verify security patches and required configurations.
Some feature of Nessus:
1.Cost:Nessus is the best free network vulnerability scanner available, and the best to run on UNIX at any price. It is constantly updated, with more than 11,000 plugins for the free (but registration and EULA-acceptance required) feed.
2.Linux Platform:Key features include remote and local (authenticated) security checks, a client/server architecture with a GTK .
3.Graphical interface, and an embedded scripting language for writing your own plugins or understanding the existing ones. Nessus 3 is now closed source, but is still free-of-cost unless you want the very newest plugins.
How Nessus uses Nmap
Nessus is optimized to work with what we call "plugins". Plugins are implemented in such a way that it does not cost anything memory-wise to launch them -- the NASL interpreter is optimized in such a way that launching a plugin only uses several kilobytes. The operating system is not involved when a plugin is created, which makes the process execution fast and painless.However, since Nmap is an external application, Nessus calls it by launching a special plugin which actually executes the nmap binary, which is a costly operation. To make things worse, in the Nessus architecture each plugin is in charge of ONE host. This means that if you have configured Nessus to scan forty hosts at the time, then there will be forty instances of Nmap running in memory.If you are familiar with Nmap and want to use it for your scan, then run it from the command-line first, and save the results in 'greppable' output:
# nmap -n -sS -p1-65535 -oG nmap-results.txt 127.0.0.1/16
You can then import the results in Nessus directly (in the plugins preferences -> Nmap NASL Wrapper -> File containing Nmap results). This will prevent Nessus from re-scanning your network. You will need the nmap.nasl plugin.
To use Nmap from within Nessus:
Download and copy nmap.nasl to your plugins directory: # cp nmap.nasl /opt/nessus/lib/nessus/plugins/
Restart nessusd: # killall nessusd
# /opt/nessus/sbin/nessusd -D
Next time you connect to Nessus, your client should display a new port scanner (Nmap NASL Wrapper). If not, then it probably means that nmap is not in your $PATH when you are starting nessusd.
You can Download NESSUS By clicking here
Tuesday, February 26, 2008 at 9:51 PM Posted by SONU MISHRA
Labels: Oracle 0 comments
Monday, February 4, 2008 at 7:50 PM Posted by SONU MISHRA
Username Password
applsys apps
ctxsys change_on_install
dbsnmp dbsnmp
outln outln
owa owa
perfstat perfstat
scott tiger
system change_on_install
system manager
sys change_on_install
sys manager
Labels: Oracle 0 comments
Friday, January 25, 2008 at 3:40 PM Posted by SONU MISHRA
Labels: SQL INJECTION 0 comments
Sunday, January 20, 2008 at 12:04 PM Posted by SONU MISHRA
Labels: HACKING TOOLS, SQL INJECTION 0 comments